Briton ran pro-Kremlin disinformation campaign that helped Trump deny Russian links


A British IT manager and former hacker(above) from Darlington ran a disinformation campaign that duped former US intelligence agents and provided Donald Trump with manufactured “evidence” to deny that Russia interfered with the US election
A British IT manager and former hacker launched and ran an international disinformation campaign that has provided US President Donald Trump with fake evidence and false arguments to deny that Russia interfered to help him win the election.
The campaign is being run from the UK by 39-year-old programmer Tim Leonard, who lives in Darlington, using the false name “Adam Carter”. Starting after the 2016 presidential election, Leonard worked with a group of mainly American right-wing activists to spread claims on social media that Democratic “insiders” and non-Russian agents were responsible for hacking the Democratic Party. The hacking attacks had damaged Trump rival Hillary Clinton’s campaign.
The claims led to Trump asking then CIA director Mike Pompeo to investigate allegations circulated from Britain that the Russian government was not responsible for the cyber attacks, and that they could be proved to be an “inside job”, in the form of leaks by a party employee. This was the opposite of the CIA’s official intelligence findings.
Trump went further at his July 2018 summit with President Putin in Helsinki, saying he believed Putin’s claim that Russia had not interfered. In doing so, he rejected multiple highly classified US intelligence agency reports given to him over the past 18 months, including by former president, Barack Obama. “I don’t see any reason … why it would be [Russia],” said Trump.
Three days earlier, the US Department of Justice (DoJ) had charged 12 Russian Federation Main Intelligence Directorate of the General Staff (GRU) intelligence officers with conspiracy against the US, releasing unprecedented amounts of previously top secret information about the agents, offices and tools used in multiple cyber attacks on the Clinton presidential campaign.
After returning to the US, facing outrage over his conduct, Trump claimed he mis-spoke and meant to say the opposite of what he said.
The Guccifer deception
The GRU’s hackers were caught red-handed in June 2016, when the Washington Post exposed evidence of their role. Within 24 hours, after the Post had asked Russia for comment, the hackers fabricated evidence and planted a false trail that the hacking was the work of an imaginary, lone Romanian called Guccifer 2.0. While this happened, GRU officers were spotted doing online searches to check English phrases while penning the first blog post for their Romanian fake, according to the DoJ indictment.
Guccifer 2.0’s role was “falsely to undermine the allegations of Russian responsibility for the intrusion”, according to the indictment. US and European intelligence agencies identified “Guccifer 2.0” as a Russian deception operation before Americans went to vote. Detailed evidence had not been publicly available until the publication of the indictment.

Guccifer 2.0 vanished the week after President Obama released intelligence confirming that Russia had helped Trump to the presidency – just a week before Trump’s inauguration in January 2017. “Here I am, again, my friends,” Guccifer blogged, claiming: “I have totally no relation to the Russian government.” Then he vanished. Tweets, blogs and tempting tips to journalists dried up.
The GRU actor playing Guccifer 2.0 tripped up, and gave his hoax away, several times. On one occasion, he made the catastrophic error of forgetting to turn on his virtual private network (VPN) before logging on to WordPress. WordPress is an American blogging service which records login addresses and can give them to the FBI. The exposed address led US intelligence directly to a GRU Moscow office.
As Trump moved into the White House, he faced growing suspicion – and now a full-blown investigation – that his campaign had been backed by Russia to help win the presidency. In Britain at the same time, archived evidence shows, Tim Leonard was completing a website intended to obfuscate the truth about Guccifer 2.0 and the GRU.
The Guccifer distraction
A Twitter account traced to Leonard revealed his new project – a campaign claiming that the hacking was done by a Democratic Party insider – on 3 February 2017. “What if #Guccifer2 is NOT Russian ... NOT even a hacker – but still had access to DCCC [democratic campaign] docs?” it said.
At 1.14am on 5 February 2017, Leonard registered the website g-2.space. He hid his involvement using nominee company Identity Protect Ltd, but was given away by internet records which showed that the site was operated from internet address 213.229.109.154, one of two UK virtual servers he ran for web design company Creative Insomnia.
His g-2.space front page went live 13 hours later, and included the hidden warning: “Contingency plans are in place in case this site or its creator are compromised.” A hidden web page comment warned: “If I die under suspicious circumstances, the primary suspects should be the Clinton cartel.”
G-2.space’s launch page listed five prominent mainstream journalists he had contacted, and who had faced demands to disclose their evidence and sources about Guccifer 2.0. All declined or ignored him.
Leonard’s website was created in and run from the UK, using servers owned by Creative Insomnia of Newport, Gwent. Leonard is listed in company records as a shareholder and director. His activity was not known of or authorised by others in the company (see below).
Leonard admits hosting g-2.space, a website which published numerous articles giving mutually contradictory and often nonsensical theories, each attempting to prove that the pretend Romanian was not a Russian disinformation invention.
Leonard also admits that he secretly built another website inside the servers he was employed to manage. His first hidden site, Defianet (d3f.uk), initially campaigned on piracy and privacy, themes familiar to programmers who had worked with him on unrelated projects and who spoke with Computer Weekly.
Defianet’s front page proclaimed “United in the shadows” when it went online in September 2014. During 2017, he transformed Defianet to make it a focus for US extremist and conspiracy “independent media” groups, many of which are notorious for spreading false news. The site also promoted WikiLeaks and Russia Today (RT), the state-owned media channel.
Leonard has created and managed a library of disinformation manuals and techniques shared with his supporters, including “Weaponisation of social media”, “Deception techniques” and “Information warfare”. He moved the library to g-2.space after being ordered to close Defianet.
Leonard, who lives in a modest red-brick house in Darlington, is the technical director of Creative Insomnia. He admits that he built websites “making use of Creative Insomnia’s infrastructure”, including g-2.space, without the knowledge of his company, a fellow director and other workers. It was “entirely my responsibility ... not a board-approved decision”, he confessed in a letter.
G-2.space claims to be written by an anonymous persona called Adam Carter. The name was copied from a character in Spooks, a BBC spy drama series broadcast from 2002 to 2011.
Computer Weekly has established that the email address used by the fictional Adam Carter – op@d3f.uk – was set up on Creative Insomnia’s email system in 2014, and used to run accounts on Reddit, Twitter and Disqus. The email used was on the same domain as Leonard’s Defianet site. As the company’s sole server manager, Leonard was the only person able to create new websites and email addresses.
Creative Insomnia
Creative Insomnia was launched as a web design business in January 2005. It is run by partners Mark Butler and Sarah Chicken, who are university lecturers at the University of South Wales and the University of the West of England. Tim Leonard joined in 2010. They currently host about 45 small sites on UK datacentres run by Simply Transit of Bracknell.
Because of this, the IP addresses which Leonard secretly used to promote his views on US politics were shared with other clients, including Newport’s gay sauna, a swinger site, Welsh businesses, and the host company.
Contacted initially in December 2017, Butler said he had no prior knowledge of Leonard’s disinformation activities. Butler said he was shocked to learn that hidden sites and email services had been secretly running on his company’s systems since 2014. He ordered them taken down. Both sites went offline within two hours. One soon reappeared online at a new site in Bulgaria, and was later moved back to the UK host Webfusion, in an IP block controlled from Leeds.
The websites had been set up “behind the backs of directors”, Butler said. There is no suggestion that Butler or Chicken previously knew about Leonard’s concealed activities.
Butler confirmed to Computer Weekly at the time that he had “disciplined Tim Leonard”. “He has apologised for using the servers,” he said. “Where we are going next, I don’t know. I have to speak to another member of the company to decide what to do with Tim,” he added.
When the Twitter account @with_integrity used the email address in 2016, the writer described himself as a “CTO/software developer/ex-blackhat” from England – a description matching Tim Leonard. During the US elections, @with_integrity and Leonard’s other accounts began circulating media attacks on Hillary Clinton, describing her as a “fracking warmonger”.
The Twitter account, which was later also given the fake name Adam Carter, trolled mainstream journalists or academics who disagreed with conspiracy theories Leonard encouraged in early 2017. On unmoderated social networks permitting hate speech, “Carter” later linked to American neo-Nazis such as “Anna” and promoters of the Daily Stormer neo-Nazi website.
One @with_integrity tweet asked for confirmation that the cyber security expert who first spotted Russian hackers was Jewish. “Social media activity patterns [suggest] possible observance of the Sabbath,” he told followers. Leonard suggested in the tweet that social media patterns implied that the researcher and Guccifer 2.0 could be the same person.
After his hidden sites were discovered in December 2017, Leonard told Creative Insomnia founder Mark Butler that he had created g-2.space for an “old friend” called Ken. In a letter, he referred to “further enquiries regarding g-2.space in relation to some points Adam/Ken has asked me to look into”.
Leonard told Butler that Ken – the mysterious friend he claimed was running the Adam Carter operation – was Ken McClelland, a programmer who had worked with Leonard in Methlabs, a group building a software firewall.
This was untrue, Computer Weekly has found. Journalists traced McClelland to western Canada, and interviewed him. Asked why he had lied about McClelland and the accounts he had created, Leonard did not reply.
Hoax hits White House
One document – a tip-off file obtained in June 2017 by Leonard’s site from an “anonymous source” – took new disinformation all the way to the White House and the CIA.
The untitled file included complex details explaining how to unlock information inside a tranche of files released by Guccifer 2.0 in London. Metadata in the files had been manipulated to “prove” that the documents could have been stolen by a Democratic National Committee (DNC) employee. Until the file arrived, the information hidden in the files, created by the GRU hackers and known only to them, had not been detected by security experts.
The document, rewritten for propaganda effect, was published three weeks later and claimed to be the work of a new fake personality called Forensicator, which claimed that stolen DNC documents were copied to a computer located in the eastern US. If correct, it was devastating news for US intelligence – because it cleared the Russians.
Some former intelligence officials, from a group called Veteran Intelligence Professionals for Sanity (VIPS), backed up the claim. A group, including William Binney, a former technical director at the US National Security Agency (NSA), and former CIA officer Ray McGovern, were persuaded, without checking the file data, to say that the hacking was the work of insiders.
According to former NSA technical manager Tom Drake, “Ray’s determination to publish claims he wanted to believe without checking facts and discarding evidence he didn’t want to hear exactly reproduced the Iraq war intelligence failures which the VIPS group was formed to oppose”. He and other VIPS members refused to sign McGovern’s report.
But the VIPS endorsement was repeated by American media, from respected left-wing publication The Nation to controversial right-wing site Breitbart News. The ploy succeeded – and made it to the White House. Binney was invited on to Fox News and said allegations that Russia had hacked the DNC were unproven. Trump then told CIA director Mike Pompeo to see Binney to find evidence to support the claims. Pompeo met with Binney on 24 October 2017.
Binney said he told the CIA chief that he had no fresh information. But he said he knew where to look – in the surveillance databases of his former intelligence agency, NSA.
As a former top NSA insider, Binney was correct, but not in the way he expected. NSA’s top secret records, disclosed in the DoJ indictment earlier this month, lifted the lid on what the Russians did and how they did it.
A month after visiting CIA headquarters, Binney came to Britain. After re-examining the data in Guccifer 2.0 files thoroughly with the author of this article, Binney changed his mind. He said there was “no evidence to prove where the download/copy was done”. The Guccifer 2.0 files analysed by Leonard’s g-2.space were “manipulated”, he said, and a “fabrication”.

William Binney (left) checks the Forensicator report with author Duncan Campbell
How Russia attacked
The GRU used multiple units to conduct “large-scale cyber operations to interfere with the 2016 US presidential election”, according to the US hacking indictment. The operations involved “staged releases of documents stolen through computer intrusions”, including by Guccifer 2.0, WikiLeaks and DCLeaks, another front observed being set up by the GRU.
Security experts have been stunned by the depth and detail of US intelligence information on the hackers in the indictment. Some of the detail could likely only have come as the results of counter-attacks on the GRU, implanting malware that was copying screens and keystrokes, at the same time they were doing the same to officials in the Democratic Party.
The main Russian attack began in March 2016, and used large-scale phishing attacks that acquired the email accounts of members of Hillary Clinton’s campaign team, including campaign chairman John Podesta. Staged releases began in June 2016.
Three days before the start of the Democratic National Convention on 22 July 2016, WikiLeaks published the first of 44,053 emails from the senior democrats’ accounts, including 17,761 attachments. Some of the emails appeared to show bias by top-level Democratic Party officials in favour of Clinton. Four top DNC officials quickly resigned, throwing Clinton’s nomination convention into disarray.
Guccifer 2.0 claimed credit, tweeting – accurately, it now appears – that WikiLeaks had published documents “I'd given them”. Donald Trump loved it, telling a Florida news conference that Russia should increase its cyber espionage: “Russia, if you’re listening, I hope you’re able to find the 30,000 emails that are missing.”
Trump repeated his view a month before US election day, telling a Pennsylvania crowd: “I love WikiLeaks!”
The Russian attacks included creating fake social media “posing as US persons... to interfere with US political and electoral processes” in order to defeat “the lawful governmental functions of the United States”, according to another grand jury indictment released in February. The indictment charged 13 Russians working for the St Petersburg Internet Research Agency – known as the “troll factory”. Impersonating a US citizen to interfere in elections is a crime in the US, irrespective of the country where it takes place.
Leonard’s @with_integrity Twitter account had also posed as a US citizen in the same period.
Darlington’s disinformation warrior
At the start of his career, Leonard (pictured left) helped create a firewall system, PeerGuardian, which was designed to block music industry investigators from infiltrating networks where computer users shared music in breach of copyright laws. Leonard worked with a group of privacy and piracy activists in Europe, Canada and the US. His online name was Method.
Leonard’s website Methlabs was used to develop and support PeerGuardian. His blog posts on Methlabs promoted Ecstasy test kits, shared cracked programs and hacks, and threatened distributed denial of service (DDOS) attacks on film industry anti-piracy teams.
Leonard was later hired to run servers for Simplyclick, a now-defunct portal which provided intranets for British schools.
Evidence recorded by the Internet Archive shows that he hid blocking lists of film industry investigators’ addresses inside Simplyclick’s infrastructure. Archived evidence from Simplyclick also refers to a Methlab tool, XS (see image below).
Methlab XS shown on Simplyclick
Leonard began creating networks of anonymous media accounts after he joined Welsh internet firm Creative Insomnia. In many of the accounts, he pretended to be a US citizen and Democratic Party supporter, posting thousands of angry, expletive-loaded comments. With a hissing cat as avatar, in August 2010 he signed up to blog host Disqus as @Retaliate. He added more anonymous Disqus accounts – @InconvenientProof and @OptimumCognition.
Leonard again offered to exploit servers he was responsible for managing. In November 2010, he told other programmers: “I can certainly host a site ... the boxes I’ve got should be able to handle a fair bit of traffic ... of course it would be free.”
Leonard has refused to explain why he started building and running profiles in which he pretended to be a US citizen. Social media activity seen by Computer Weekly shows that he subscribed to US conspiracy theory sites, including Breitbart News, Infowars and Bulltruth.
After building Defianet’s website, he added a new Disqus account – @Inviolable – and joined Reddit as d3fi4nt (Defiant). Both accounts used his Creative Insomnia email address, op@d3f.uk. On Reddit, d3fi4nt posed as a US-based Democrat supporter of Bernie Sanders, publishing hate messages targeted at Clinton, and signed up to The Donald, an exclusive Reddit location for Trump supporters, as well as r/Conspiracy, a notorious watering hole for conspiracy theorists.
On Disqus, @Retaliate and @InconvenientProof posted attacks on Clinton, following the same messaging at the same times as known Russian trolls. @InconvenientProof and d3fi4nt also operated as sockpuppets, referencing other Leonard-operated accounts and activity. @OptimumCognition focused on media industry claims to be losing revenue to pirates, writing: “Prove your alleged losses ... or shut up and fuck off.”
His @Retaliate and @InconvenientProof Disqus accounts participated in alt-right US news groups, including Breitbart News Network, a far right-wing internet platform managed until January 2018 by former Trump advisor Steve Bannon. Disqus adopted a hate speech policy to deal with the Breitbart group in 2017 after it was described as “one of the vilest cesspools on the internet ... the worst of humankind” for supporting racism and neo-Nazis.
On a Creative Insomnia domain called ciuk.eu, Leonard created multiple private personal mailboxes, using initials and false names. According to the website Have I been pwned?, email address t@ciuk.eu subscribed to games hacking websites PS3hax and Multiple Game Player Hacks (MGPH) in 2014 and 2015.
On a single day in 2015, Leonard created two new Disqus accounts using ciuk.eu addresses: @InconvenientProof, linked to tix@ciuk.eu; and @OptimumCognition, linked to a ciuk.eu mail address for a Sarah Thomas.
IP addresses used to log in to these accounts, seen by Computer Weekly, showed that the user often used a VPN anonymiser service. When, like Guccifer, Leonard forgot to switch on his VPN, he was using addresses provided by Virgin Media broadband in the UK. Fixed Virgin IP addresses used were assigned to Haughton Le Skerne – the small Darlington district where Leonard purchased a house in 2007.
Defianet proxy page
At first, Defianet looked like the work of an ambitious hacktivist. The site focused on torrents and security, advertised discussion fora, claimed to run unique “d3fcrypt” encrypted chat channels, as well as a torrent “magnet link collection” called MASS.
A “proxy relay” offered to users was built inside Creative Insomnia’s systems (see image above). The Defianet link was running at the time of publication, and is archived here. Logged in test users included Method and Retaliate.
Defianet’s original front page (see image below) stated that it was created by m3th0d (Method) and three others. Method is Leonard’s nickname. On Reddit, Disqus and Twitter, Leonard published the email address op@d3f.uk. Emails sent by that account passed through Creative Insomnia’s mail server, mail.creativeinsomnia.co.uk.
Defianet’s original front page
“I’m with integrity”
As US election campaigns ramped up in May 2016, Leonard’s Defianet email address, op@d3f.uk, was used to create a new Twitter account, @with_integrity. The name, he said, was a parody of Clinton’s campaign slogan, “I’m with Hillary”. The profile displayed a WikiLeaks avatar.
For 10 days in 2016, @with_integrity trolled and attacked the Democratic Convention, accusing the Democrats of collusion, conspiracy, cheating, corruption, rigging elections and sabotage.
On 22 July 2016, @with_integrity tweeted a link to the Russian propaganda and news channel, RT, claiming that primary elections had been rigged. On 26 July, as delegates voted, @with_integrity tweeted a new RT attack on Hillary Clinton.
After Clinton was nominated, @with_integrity followed the Russian trolls’ path in supporting Donald Trump, retweeting Trump slogans, including #CrookedHillary, #LockHerUp, #MakeAmericaGreatAgain and #VoteOnlyTrump, and a third link to a “special episode” on RT.
Two months after g-2.space was launched, Leonard’s @with_integrity Twitter account also started claiming to be run by Adam Carter. The previous WikiLeaks symbol was replaced by angular lettering (IWI – I’m with Integrity) created in an obscure typeface called Critical Mass LDR. Leonard used the identical typeface to create Defianet’s logo and for a special program used by “Carter”, which he called Hexcell (see image below).
Obscure typeface Critical Mass showed link betweeen different deception sites
Fragments of Hexcell were left inside Creative Insomnia’s servers after Leonard was ordered to shut down Defianet. Leonard has admitted that he ran the Hexcell program from his personal folder inside Creative Insomnia, called Timtest. Leonard created the Hexcell program in a failed attempt to find data proving Guccifer was a former Democratic Party manager.
On g-2.space, Leonard published multiple contradictory descriptions of who Carter was supposed to be. His blog first claimed: “I am NOT a journalist or reporter ... I’m just a civilian that noticed some oddities.”
Days later, it claimed the opposite: “An independent, investigative ‘citizen journalist’ from the UK.” Meanwhile on Twitter, “Carter” described himself as a chief technology officer (CTO), a software developer and ex-blackhat, an Englishman living in England – an accurate description of Leonard.
“[I was] schooled by other hackers while working as a software developer and maintaining servers,” Leonard posted on Disqus in 2011, as @Retaliate. Last month, his Carter account claimed on Steemit: “I know what it feels like to have unauthorised access to hundreds of servers that you’re not supposed to have access to. Fortunately, for the past 15 years, I’ve been working in IT in a far more legitimate capacity and currently manage an array of servers.”
Hacking to gain unauthorised access to computer stystems – blackhat hacking – is an offence in the UK under the Computer Misuse Act, punishable by a maximum of 10 years in prison and a fine.
A bucket of conspiracy theories
Leonard’s first theory about Guccifer 2.0, posted to Reddit’s “r/conspiracy” subreddit in October 2016, was that “the feds (FBI) did it”. Guccifer 2.0 (G2) was really being used by the FBI, similar to compromised Lulzsec hacker Sabu in 2011, he claimed. Leonard had blogged at the time that he was the first person accurately to spot that the FBI had got control of Lulzsec.
In February 2017, Leonard’s g-2.space site proclaimed “Game Over”. On Reddit, he threatened a campaign of “disruption” against media outlets unless they agreed to stop reporting the US intelligence assessment on Russia, or failed to report as fact his theory that Guccifer 2.0 was a Democratic Party insider.
“Media entities will then be given seven days from confirmation of receipt to clean up their act and cease reporting” – otherwise, he would “red card violators”, he told Reddit.
The second theory, published on g-2.space, was that G2 could not be a hacker, because a stolen DNC “opposition research” file published on 15 June 2016 “took a mere 30 minutes to go from a DNC contractor creating documents to Guccifer2”. This theory was unfounded.
Leonard’s third theory involved the program called Hexcell, which he had installed on a Creative Insomnia server. Hexcell’s purpose was to decode “binary large objects” to prove that G2 was “a misdirection effort”. He tweeted Goo.gl short links using the program to hashtag #Guccifer2.
When run, the links accessed cached copies of analyses stored inside Creative Insomnia. The cached copies recorded giveaway internal filepaths to his Timtest folder (blocked from external access). After Leonard admitted creating the Timtest folder and the giveaway Hexcell links, the files disappeared.
Theory number four claimed that the DNC was hacked by Crowdstrike, the security company it had hired to kick out the Russian hackers. Four days later, according to g-2-space theory number five, a group of Ukrainians were claimed to be the real hackers – citing evidence that they had visited the White House on the day of the hack.
His g-2.space site then complained to 100 US senators that they had ignored his finding that the hacking could not have been done by Russians. None were interested. He then circulated 150 foreign ambassadors in London complaining of a “serious ... threat to global stability” if his theories were “not investigated properly”.
The g-2.space theory that worked – the theory that President Trump pushed to the CIA – was based on a unique document dump by Guccifer 2.0, in Britain.
Guccifer appears in London (not)
On 20 August 2016, UK conference organisers PSBE Events, part of iMember Media group (iMM), announced a world exclusive. They had booked the world’s then most notorious hacker – Guccifer 2.0.
Guccifer 2.0 would appear in person for the first time, they promised, in a video “live stream” at their September conference in London, Future of Cyber Security Europe 2016. Publicity for his talk, called Hacking Insights from Guccifer 2.0, generated “an awful lot of excitement”, they tweeted.
The GRU team had three weeks to decide what to say and do in London, after getting the conference invite. They played up a theory which had started to circulate in obscure conspiracy-focused chat-rooms on 4chan and Reddit, placing blame on Seth Rich, a then recently murdered DNC employee, for the DNC leaks.
Two bullets in the back had taken the life of 27-year-old DNC researcher Rich, as he walked home from work late at night in Washington. The date, significant to how his death was later exploited, was 10 July 2016. Six weeks later, in a private message exchange with Guccifer 2.0 published by a US actress, the pretend hacker referred to Rich’s death and claimed, “His name is Seth, he was my whistleblower”.
Rich’s bereaved parents have repeatedly pleaded for the torrent of conspiracy claims about their dead son to come to an end. “Anyone who claims to have such evidence is either concealing it from us or lying,” his father Joel said, adding: “They have a transparent political agenda or are a sociopath.”
WikiLeaks founder Julian Assange also planted a public pointer to Rich, after Guccifer 2.0 claimed to have provided the stolen DNC emails to WikiLeaks – a claim also shown to be accurate, according to evidence described in the latest US indictment. On 9 August 2016, WikiLeaks tweeted a $20,000 reward offer for information leading to the conviction of Rich’s killer. WikiLeaks had previously offered rewards for leaks, but never, before or since, used the tactic to point to a possible confidential source. WikiLeaks attempted to backtrack the next day.
Forensic analysis of the files prepared for the conference suggests that the GRU team then hoped to exploit the London conference opportunity by framing Rich.
By early September 2016, Guccifer 2.0’s operators had 2,280 stolen DNC files ready to publish at the conference. None of the files concerned Rich or his work. File internal data analysis shows that they were all stale, deadwood information, and of no relevance in 2016. All had been completed and closed before the previous presidential election in 2012.
Using a combination of copying and compression techniques, the “last modified” timestamps of all but 12 of the aged files was changed to 5 July 2016, just five days before Rich was killed and 17 days before WikiLeaks published its first share of the DNC hacks. While this was done, the computer in use for copying had its clock set to Eastern Daylight Time (EDT), the zone covering Washington DC and the eastern US seaboard.
Conference organisers had previously asked former British hackers to present the speech, but they declined. Mustafa Al-Bassam, a former hacker from the Lulzsec group, said: “I didn’t want to be a representative for potentially illegal hacking activities.”
News teams arrived at Prospero House, a conference centre near London Bridge, on 13 September 2016, and were disappointed. There would be no live streaming. Instead, the hackers had sent the organisers instructions, including a prepared speech, a PowerPoint show published here for the first time, and a link to a uniquely structured compressed file of stolen data.
Conference presenter Tim Holmes read Guccifer’s long, rambling, ungrammatical statement. Holmes displayed a slide giving an internet address from which to download the files, and the password to unlock them (see image below).
Tim Holmes shows slide giving url from which to download files
Guccifer’s PowerPoint presentation, a pseudo-hacktivist rant, mixed much-derided Comic Sans lettering with images lifted from TV’s Mr Robot. The Guccifer script claimed that the hacks had exploited flaws in NGP-VAN, the voter analysis system used by the Democrats. This claim was not supported by an explanation, or by the contents of the stolen files, and has been refuted by the company.
Mark Hilton, solicitor for iMM group and Cyber News, told Computer Weekly: “My client simply invited [Guccifer 2.0] to present at the conference. My client did not stipulate or dictate the concept of the presentation. My client ... was never informed as to the existence and content of the hacked information/data.”
When users on Twitter asked how to open the hacked container of DNC files, the Twitter account run from Leonard’s d3f.uk’s email server – @with_integrity – tweeted the password “for anyone struggling”. The password was GuCCif3r_2.0 – the fake hacker’s name in “leet speak”.
How the Forensicator fraud worked
The team that created Forensicator, including Leonard, gave away that they were not the real authors of the analysis when they inaccurately copied a Linux “Bash” script they had been sent, breaking it. This suggested that they did not write, understand, or test the script before they published. Someone else had sent the script, together with the fake conclusion they wanted discovered and published – that DNC stolen files had been copied in the US Eastern Time zone on 5 July 2016, five days before DNC employee Seth Rich was killed.
Uncritical reporters failed to spot that the Forensicator blog gave no evidence for its conclusion, which was that the data analysed was evidence of theft by local copying happening within the eastern US. The Forensicator report avoided pointing out that the time stamps examined were present only in the special London group of documents, and not in tens of thousands of other DNC files published by WikiLeaks or Guccifer 2.0.
The files were manipulated using an unusual method of file packing, forensic checks show. Because of computer clock settings, the packing operations appeared to have created “evidence” that the stolen files had been copied in the US Eastern Time zone, which includes Washington.
US Eastern Standard Time (EST) is normally five hours behind Coordinated Universal Time (UTC) – better known in Britain as Greenwich Mean Time (GMT). In summer months, clocks are set forward, placing the US Eastern Daylight Time (EDT) four hours behind UTC. The difference between a time zone and UTC is the offset. It is trivially easy for any computer user to change their time, date and time zone offset, using standard controls.
The files released in London, we found, had first been processed in this way to show timestamps for 5 July 2016. Some 13 groups had then been compressed using WinRAR 4.2. Nine additional files were compressed using 7zip. The archive, called 7dc58-ngp-van.7z, was published in this format, as a single file of 680MB.
This dual compression method was unique to the London documents. It was not used in other file dumps released by Guccifer 2.0, WikiLeaks or other publishers of stolen DNC material. The special method used two different file compression systems, 7zip and WinRAR, and required using a four-year-old, superseded version of WinRAR to obtain the required result. The way the Russians did it, the two compression operations appeared to overlap within a single 20-minute period. The tampering may have been done on 1 September, a week before the London conference.
On inspecting the full data analysis, Binney agreed: “It’s clear G2 is messing with the data. Everything G2 says is suspect and needs to be proven by other sources/means. I agree there is no evidence to prove where the download/copy was done.”
He added: “The merger of data from 5 July and 1 September ... makes all the G2 crap a fabrication ... we should only say what we can prove with evidence.”
[Updated 13 August:] Binney subsequently repeated and confirmed his views in an interview with the Lyndon LaRouche Political Action Committee, a campaign vehicle for the controversial seven-time presidential candidate Lyndon LaRouche.
Privately, Binney says his colleague Ray McGovern, who has also pushed the Forensicator theories, accepts that there is no evidence where the files were really copied. “Ray no longer argues that point – except to call it an ‘alleged location’,” said Binney. McGovern has refused to confirm this, or to answer questions about evidence for his claims.
Despite accepting that there was no evidence, Binney and McGovern have not retracted the claims in the 2017 VIPS report at the time of writing.
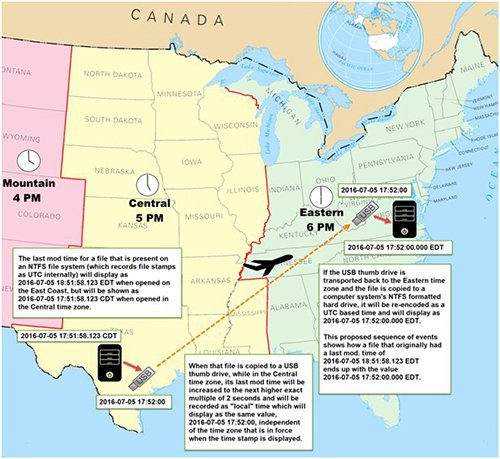
In a bizarre and telling sequel, a retired engineer later spotted that some files released in London had popped up a second time in a batch of so-called “Clinton Foundation” files published by Guccifer 2.0 in October. But the file modification times were one hour different. This happens if computer time zone settings are being manipulated as files are copied and recopied, as described above. This was an inconvenient truth. Accepting that the engineer, Steve McIntyre, was factually correct, the Forensicator came up with a comic and far-fetched explanation to avoid talking about clock tampering.
Their explain-it-away theory was that in 2016 their alleged DNC leaker had transferred the aged problem files from Washington to a computer using US Central Time, one hour behind DC time. The leaker then copied the files to a thumb drive in the Central Time zone, flew “back to the East Coast” and copied it again for public release. To assist readers’ understanding, they published a large map showing how to fly memory sticks from Washington to New Orleans, and back again (see image below).
Fantasy explanation of timestamp faking
The obvious, simple explanation was that hackers were manipulating computer clock settings. The observed changes would have taken seconds.
A hike to the Rockies
It took a month to locate Ken McClelland, the Canadian programmer who Leonard told his boss was the real Adam Carter – the friend he claimed to have built the sites for. With the assistance of Canadian TV company Global, we found and spoke to McClelland.
McClelland lives in Kelowna, a scenic British Columbia town in the eastern Rockies, astride Canada’s main east-west highway.
Leonard’s claim that McClelland was the real Russian disinformation agent had initially appeared to have substance. At the time Leonard and McClelland worked together, McClelland’s online name had been d3f, as used in the Defianet site name, d3f.uk.
Leonard and McClelland, then 16 years old, had worked together to build PeerGuardian, the firewall system designed to block music industry investigators from infiltrating P2P networks.
Leonard was “lying”, says McClelland. Leonard had “set him up to cover himself”. He had never heard or known of d3f.uk or Defianet. McClelland added that he had stopped using d3f as an online nickname by 2010, he and Leonard had never met in person, and Leonard had not asked for permission to use his online name.
“I haven’t talked to the man in a decade. It’s a pissoff,” McClelland added, in the TV interview.
Responses
In a letter admitting setting up the hidden Creative Insomnia sites, Tim Leonard wrote: “No crime has been committed by myself nor has any crime been committed through those sites.” Computer Weekly is not suggesting that Leonard or any of the websites associated with him has committed any crime.
Last December, after another IT publication asked about Carter, staff received threats, sent through Creative Insomnia’s email systems, managed by Leonard and signed Adam Carter.
The emails threatened: “I can generate a lot of noise... I already have an article prepared. I am prepared to write a much more muted, sanitised version that won’t inherently be propagated by a bunch of independent media outlets ... all depends on how everyone else wishes to proceed.”
If a story was published, he said, the publication would “end up spontaneously combusting”, and the author of this article would “burn”.
When Leonard was called, he claimed the author of this article was an “American-style Russiagater”. On Imgur, Leonard published all the enquiries sent to “Carter”, accompanied by his own evasive responses. On Twitter, “Carter” published part of an email addressed to Leonard.
Two days later, the “Carter” operation merged with Disobedient Media, and Carter appeared on the site as a “technology correspondent”.
Leonard’s other responses have been revealing about his operations. Within two hours of being approached and photographed by the Sunday Times at home in Darlington, the Adam Carter account was used to tweet: “I’m anticipating character attacks, straw man attacks and other flak from MSM [mainstream media] outlets. Of course, I’m not anticipating they’ll focus on the evidence and research raised.”
Within two hours of a Computer Weekly editor asking Leonard’s company for comment, the Carter account clicked to start following him on Twitter.
Last week, Computer Weekly sent Leonard a detailed email for comment, addressed to him as Mr Leonard, to his Creative Insomnia email address and his defianet@protonmail.com email. The reply was signed “Adam Carter” and came from the email address defianet@protonmail.com, which Leonard has used since the start of 2018. Leonard did not respond to the specific questions we asked.
As Carter, he has tweeted: “Those behind Guccifer 2.0 sacrificed their own hacking claims in an effort to point out that Seth Rich had dealings w/Russians when alive.” On Reddit, as “d3fi4nt”, he has stated his target: “To be clear – I believe Seth Rich was the source for the DNC leaks.”
According to US deputy attorney general Rod Rosenstein when releasing the latest indictment, the hacking and disinformation activities he described were part of a larger plan to “spread divisive messages” and to “spread disinformation and to sow discord on a mass scale in order ... ultimately to undermine the appeal of democracy itself”.
Additional research: This extensive investigation would not have been possible without essential help from Global Kelowna TV, Canada; Global TV video journalist Kelly Hayes; data and forensic analysis by programmer Matt Fowler; media network analysis by Lawrence Alexander; and research assistance from former hackers Lauri Love and Mustafa Al Bassam.
Note: This article was updated on 7 August to make it clear that former Trump advisor Steve Bannon managed Breitbart News Network, but was not its founder, and that Disqus did not expel Breitbart, but created a hate speech policy in 2017 after Breitbart was criticised for supporting racism and neo-Nazis.
The US disinformation team
Disobedient Media is a so-called “independent media” site that describes “Adam Carter” as its technology correspondent. It claims to “bring honesty and integrity back into journalism”. The site has recycled paedophile allegations directed at Hillary Clinton and fellow democrats, and has made repeated attempts to frame murdered DNC official Seth Rich.
Newspapers in France, Germany, Spain and Britain have identified Disobedient Media as an epicentre of Russian-backed attacks on Europe, using forged documents, including smears against Angela Merkel, Sadiq Khan and Emmanuel Macron.
The site, which has run since Trump took office, claims to be run by four young Americans whose records say they each live with their parents. Co-founder and head researcher Ethan Lyle, 23, registered the business name to his parents’ house in a remote part of rural Iowa’s plains. Lyle is no longer listed as a member of the team.
Disobedient Media was started by William Craddick, who claims to have been the prime spreader of a conspiracy story known as Pizzagate, which claimed that Hillary Clinton and her election staff ran a child sex and torture ring in the non-existent basement of a Washington pizzeria.
On startup, Craddick publicised a Pastebin dump of false information claiming that Angela Merkel was bringing ISIS terrorists into Europe so that she could unleash an “EU Army” against other EU states. The article displayed Merkel appearing to give a fascist salute (pictured left).
Following the Westminster Bridge terror attack, Craddick published false claims that London mayor Sadiq Khan was linked to ISIS and the Muslim Brotherhood. In September, Disobedient Media reported that cancellation of the Catalan referendum had put in doubt Spain’s membership of the EU. The report was identified by El Pais as Russian disinformation. Craddick has also tweeted fictitious quotes never spoken by Winston Churchill.
The day before the French presidential election, which took place on 5 May 2017, Disobedient Media was chosen as the channel to release 9GB of hacked email and files from associates of now-President Emmanuel Macron. According to the new US indictment, one of the officers whose name leaked into Macron’s hacked mail, Georgy Petrovich Roshka, was an employee of GRU unit 26165 and also took part in the DNC attacks – further, if indirectly, connecting Leonard to the Russian disinformation activity.
Updates: Two days after publication of the Computer Weekly article, Russian government news agency Sputnik News confirmed that Adam Carter’s real name was Tim Leonard. In an interview on the channel’s Faultline programme, Disobedient Media editor-in-chief Elizabeth Vos was asked if Tim Leonard was indeed Adam Carter, and she said: “That is correct.”
In e-mails Leonard then sent from Creative Insomina Ltd to the editor of Computer Weekly Bryan Glick, he confirmed that he was "Adam Carter".